Pi-hole - Blackhole and Sinkhole Host and Domains
Note: This
is an update from my ISC Diary
published 25 February 2018
I checked the hardware requirements and already had a server I could install this on. I used CentOS 7.4 as my platform but before starting, make sure selinux isn't running because it isn't supported (It is one of the checks the installation script does). To check execute:
# sestatus
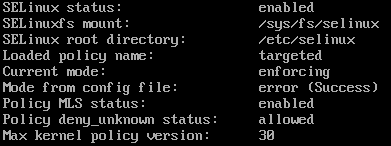
If it return enabled change the configuration (see below) and reboot after it has been saved:
# vi /etc/sysconfig/selinux
set selinux=disabled
Next make sure your server has a static address before running the installation and then you are ready to install.
I followed their recommended installation command: curl -sSL https://install.pi-hole.net | bash [1] but you can also install everything manually by following the steps here as Method 1 or 2.
The installation was pretty straight forward and it checked for any missing packages and added them to the server. I answered a series of question to setup the Pi-hole DNS server. After the installation you need to point all your clients to your new DNS server (forward internal DNS server to Pi-hole) to take advantage of the blocking capabilities.
Changing Pi-hole Password
If you setup the web interface you can login via http://IP/admin and login with the default password provided after the installation (the password can be changed at the command line with: sudo pihole -a -p) or view the statistics via the Dashboard provided by the web server.
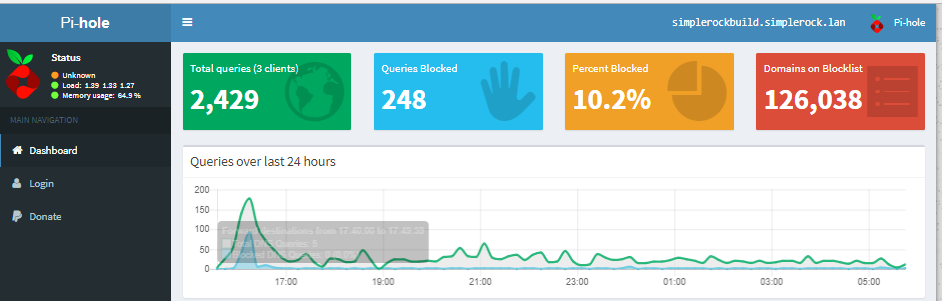
CentOS Additional Configuration
If you want to add known lists of bad domains, you need to do the following updates in order to add them or manually update your list via the interface. You need to change the following settings in sudeors
# sudoedit /etc/sudoers
·
#Defaults requiretty
# Allow apache to update Pi-hole
·
apache
ALL=(ALL)NOPASSWD:/usr/local/bin/pihole
As user root, add a cronjob for Pi-hole to update daily
# Update pihole block lists
* 1 * * * /usr/local/bin/pihole -g > /dev/null 2>1&
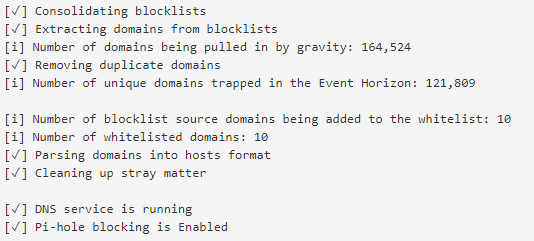
Adding Other Blacklists
These lists can be added in Settings → Block Lists with the list that are already presents
· http://osint.bambenekconsulting.com/feeds/c2-dommasterlist.txt
· http://www.malwaredomainlist.com/hostslist/hosts.txt
· http://malc0de.com/bl/ZONES
· http://mirror1.malwaredomains.com/files/justdomains
· https://isc.sans.edu/feeds/suspiciousdomains_High.txt
· http://osint.bambenekconsulting.com/feeds/dga-feed-high.csv
· https://raw.githubusercontent.com/jonschipp/mal-dnssearch/master/mandiant_apt1.dns
Update Pi-hole
To update Pi-hole, execute the following command
# pihole -up
To view the update log
# cat /etc/pihole/install.log
Known Error – lighttpd will not start
# vi /etc/lighttpd/lighttpd.conf
Comment out this line: #include_shell "cat external.conf 2>/dev/null"
Restart service:
# service lighttpd status -> Check for webserver issues
# service lighttpd restart
# service lighttpd status -> Check for webserver running
[1] https://pi-hole.net
[2] https://discourse.pi-hole.net/t/hardware-software-requirements/273
[3] https://github.com/pi-hole/pi-hole/#one-step-automated-install